Passwords, together with usernames, are still the main data used to access online accounts. Poor password management is also one of the main causes of accounts of individuals and companies being hacked. In this article, we list recommendations for good password management, thus ensuring greater protection for your accounts.
The evolution of passwords
Simple passwords stored without security
Initially, passwords were short and stored in plain text (without any form of encryption) in systems. Any intruder who gained access to the database where they were stored could easily view these passwords since they were saved in a readable format. Since people often used the same email and password across multiple systems, these intruders could access various accounts of the same individuals with little effort.
Hashing and encryption
The systems started converting passwords into hashes, using cryptographic hash functions. In other words, the password is no longer stored, only its hash. Every time the user logged in, their password was converted into a hash using the same algorithm, and that hash was compared with the one stored in the database. This ensured that, even if an attacker obtained the file or database, they couldn’t easily recover the original passwords, since the hash functions are irreversible.
Later, it was realized that, although switching from storing passwords to storing their hashes was a significant step at the time, it was not enough to securely store user credentials. This was due to an attack known as rainbow tables, where attackers had precomputed tables of hashes and their corresponding plaintext equivalents. To address this, it is now recommended to add a salt to the password and then hash the combination of the password and its salt. This ensures that even if two users have the same password, the result of the password + salt will produce a different hash, making it much more difficult to crack.
Increased complexity
Since users were creating passwords that were too simple, it became possible to discover them using brute force or dictionary attacks. As a result, companies started implementing policies that required frequent password changes (at least every 90 days) and increased password complexity. This meant passwords had to include uppercase and lowercase letters, numbers, and special characters. Additionally, the reuse of previous passwords was also prohibited.
Multifactor Authentication (MFA)
Due to the increase in phishing attacks and keyloggers, Multi-Factor Authentication (MFA) was introduced. This meant that, in addition to the username and password, a second factor was required, such as a code sent via SMS to the user’s mobile phone or a hardware token.
One-time password systems (OTP) such as Google Authenticator(Android; iOS) and Microsoft Authenticator(Android; iOS) have also started to be implemented.
Password Managers
As the number of accounts for each individual increased, password management systems began to emerge. These systems allowed passwords to be stored securely (using advanced encryption) and organized efficiently, while also providing a simple way to access them.
In addition, these systems included a password generation feature, allowing users to create long and complex passwords without the need to memorize them. They also encouraged the use of unique passwords for each system.
Elimination of passwords and biometrics
Currently, we are witnessing a transition to passwordless authentication. Protocols like FIDO2, which are highly resistant to phishing, allow for authentication without the need for passwords, using passkeys and physical security keys, such as YubiKeys, among others.
This approach makes the authentication process not only more secure but also simpler, utilizing methods like biometrics—such as fingerprint scanning or facial recognition.
However, in the present, we still see the mistakes of the past being repeated.
Unfortunately, even today, there are systems where passwords are stored in plaintext or hashed without a salt; individuals and companies that have not established a secure minimum password length; and a low adoption rate of Multi-Factor Authentication, whether due to systems that still lack this feature or users who have not activated it even when it is available.
How long does it take for a password to be cracked?
The following graph illustrates the strength of various passwords, highlighting that length is what provides the most strength, making it increasingly difficult to guess with each additional character.

You can test some passwords and see how long they would take to be discovered here.
What are secure passwords?
The answer to this question has changed over time. For example, in 2003, when NIST Special Publication 800-63, Appendix A was published, it was recommended that passwords should contain uppercase and lowercase letters, at least one special character, and at least one number. It also advised that passwords should be changed frequently, at least every 90 days.
This led most users to substitute certain characters with numbers, which ultimately became highly predictable, even for software designed to guess passwords. Knowing these substitutions, programmers incorporated them into their algorithms as well. This could result in a password like “P@ssW0rd123!”, which, for example, can be discovered in just 6 minutes today!
The requirement to change passwords every few days led users to simply add or replace a single character while keeping the rest of the password the same, which does not significantly enhance security.
The cartoonist Randall Munroe published a comic strip on xkcd that became popular by showing that the password “Tr0ub4dor&3” (something like Tr0v4d0r&3, i.e. minstrel with substitutions and additions) could be guessed in just three days, due to the predictable use of upper and lower case, substitutions of characters for numbers and the use of special characters, while the password “correct horse battery staple” would take 550 years, commenting at the bottom that “After 20 years of effort, we have correctly trained everyone to use passwords that are difficult for humans to remember, but easy for computers to guess.”
You would probably agree that the passphrase “correct horse battery staple” is easier to remember than the password “Tr0ub4dor3”, especially if you visualize an image related to it.
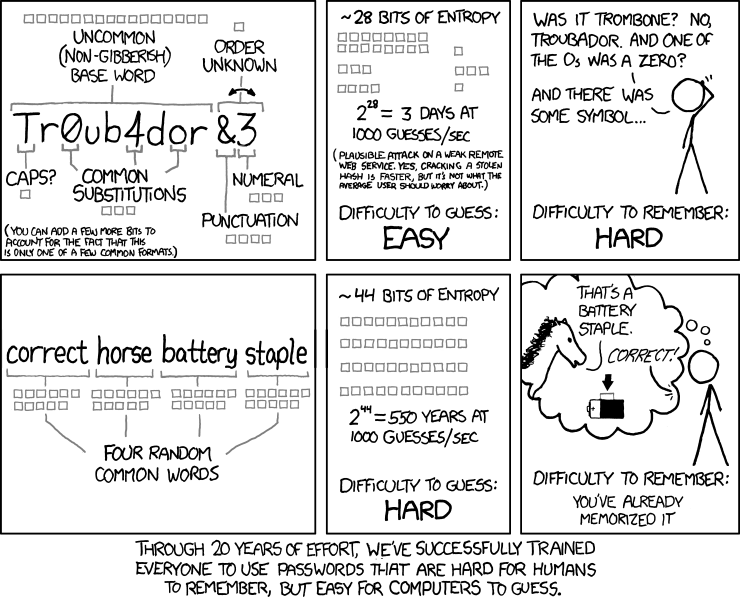
The author of this document, Bill Burr, later expressed regret over these recommendations, which were misinterpreted and led users to adopt predictable practices, even though his suggestions aimed to make passwords more robust.
The National Institute of Standards and Technology (NIST) published a new document, known as NIST Special Publication 800-63-3, in 2017, which was revised in 2020. This document is widely adopted by the industry as a reference for authentication management and identity security.
Use long passwords
One of the main factors, if not the most important, that makes a password secure is its length. The more characters it has, the harder it is to guess.
Short passwords are easily guessable in an attack known as brute force, where software tests all possible combinations of characters. It’s a time-consuming process, but it can yield quick results, especially when the passwords are too short.
Nowadays, none of your passwords should be less than 14 characters.
Ideally, you should create passphrases instead of passwords, using a phrase. Combining words like “I Love YourInfoSec Blog” can result in an excellent password.
Use random words
Avoid using passwords that contain words related to you or someone close to you. These words are often the first to be tried, especially based on what an attacker knows about you (for example, information shared on social media).
In other words, creating passwords based on information that can lead to you makes them easier to guess. Therefore, it is good practice to ensure that passwords do not include the account’s username, your name or that of close family members, your date of birth, your phone number, and so on.
The goal is to choose a passphrase that contains words that don’t form a logical connection, making it difficult for any system to guess them.
Replacing characters with their numeric counterparts no longer works effectively
At one point, some characters were substituted with similar-looking numbers, such as replacing “E” with “3” and “T” with “7.” However, just as account owners made these substitutions, software used by attackers was also programmed to do this. For this reason, such substitutions no longer provide strength to passwords.
Don’t repeat passwords
One of the main mistakes people make is using the same password for multiple accounts. Imagine that someone discovers the password for one of your accounts. With your username or email, they can easily try the same password across a range of other services.
In other words, for example, if you use the same password for Instagram and Gmail, if someone discovers your Gmail account, they can also access your Instagram account. Not only could they read your emails, but they could also see your Instagram conversations and potentially post on your behalf.
If you use business systems, it is crucial for both you and the company you work for not to use the same passwords for your personal accounts as you do for your business accounts, and vice versa. This is for similar reasons as mentioned above: if any of your personal accounts are compromised, it becomes easier for your business accounts to be compromised too, which can have severe consequences for the organization. On the other hand, if the company’s accounts are compromised, the attack could extend to your personal accounts, which I’m sure you want to avoid!
All of this can be easily resolved: each account should have a different password from all the others.
Don’t reuse passwords
At this point, what I want to emphasize is not to use passwords that you have used in the past. They likely have some trace on your side or in the systems where you used them. Let your imagination run wild and create new passwords.
Organizations should not mandate password changes. However, this does not mean you shouldn’t change your passwords when necessary.
NIST, along with other organizations, does not recommend mandatory password changes based on studies showing that this practice often leads users to adopt predictable and weak passwords. Password changes are only recommended if there is a suspicion that the password has been compromised.
Therefore, they encourage organizations not to require frequent password changes, in contrast to the previous recommendation that mandated changes at least every 90 days. They complement this recommendation by advocating for the use of Multi-Factor Authentication.
Users are no longer required to change their passwords, but they should keep in mind that one way to ensure that unauthorized access is not continuous—especially if they are unaware of such access—is to periodically change their passwords. This is particularly important for services that still do not have MFA available (which, unfortunately, are still many), but also for those that do, as we know that certain MFA methods can be vulnerable.
Pay attention to where you register your passwords
Never store your passwords in plain text, without encryption. For example, you should never record them:
- On paper, like post-its;
- In the notes app on your computer or cell phone;
- In spreadsheets;
- On the covers of mobile devices;
- Etc.
If you do this, anyone with access to the paper or your session, whether physically or remotely, will be able to read the password. In fact, this is one of the most common mistakes. It’s quite convenient, as the password ends up on a sticky note attached to the monitor or in a file on your computer’s desktop, ready to be copied to the login page… by you and anyone else who can access it, as it is completely legible.
The ideal way to combat this and maintain even more simplicity is to use a password manager, as discussed further down in this article.
Don’t save your passwords in your browsers
Browsers offer credential storage functionality to simplify the user’s experience. However, this practice is not recommended, as many do not employ robust encryption methods, and someone with physical access to the machine can extract them.
Don’t share your passwords, but if you do, do it securely
If you share your Netflix account password with a friend so they can watch some movies for free, and you use the same password for Gmail, you can see the potential risks, right? It’s not just about your friend, who may be honest; can you be sure they will store that password securely?
Especially in the corporate world, it is common for users to share their passwords with colleagues when they go on vacation or are on leave, so that others can follow up on emails and other matters. Don’t do it! If you are responsible for a department or have the ability to enforce security policies, prohibit this practice. Instead, employees should request the IT department to forward emails and calls from the absent person to their replacement.
The truth is that the more people you share your password with, the greater the risk to your account. I don’t know if you store your passwords securely, but remember that the person you share your credentials with may not take the same precautions.
Remember: the responsibility for protecting your account is not only of the service provider or your company’s IT department (if applicable); it is also yours.
In any case, there are times when you may need to share a password. In these situations, avoid using email and SMS as channels! Instead, use password managers like Proton Pass, 1Password, NordPass, etc., which offer secure password sharing features, or use secure messaging apps like Signal or Telegram.
Use a Password Manager
Password managers allow you to store all your passwords securely (with data encryption), simply, and in an organized manner, making it much easier to manage your credentials. Trust me, when used properly, they are a true game changer.
With a password manager, you only need to remember one password: the master password. Yes, just one—the one you need to decrypt all your other passwords. This password should be long and complex, but you must ensure it’s one you can remember, as forgetting it could mean losing access to all your other passwords.
So, what difference does it make to create your other passwords with 30, 40, or even 60 characters? I know this may seem daunting or even ridiculous to some, but give it a try. It won’t affect you at all, as your password manager will automatically fill them in, or you’ll just need to copy them. You won’t have to memorize or type them out, and you’ll have the confidence of using a secure password! Of course, this assumes the service allows such long passwords. Unfortunately, many services still restrict passwords to only 8 or 10 characters, which is quite unreasonable.
You can organize your passwords into vaults. For example, you might have one vault for your personal account credentials, another for your spouse’s credentials, one for your children, another for work, and so on.
You can use browser extensions that automatically fill in your credentials on the websites you visit. The most well-known password managers offer extensions for the most commonly used browsers.
They also have mobile apps that perform the same function for the apps installed on your phone, whether it’s Android or iOS.
They can be local or cloud-based. If you still don’t trust the cloud enough to store such sensitive data, you can use password managers like KeePass, where the database stays only on the device it’s installed on. However, if you want to access the data on another device, you’ll need to copy the database to that device. This can be impractical, as you will have to update both devices whenever you add or change a password or copy the database again. Some people use file-sharing services to sync between devices this way, but it’s not as straightforward as using a cloud service like Proton Pass, 1Password, NordPass, and others.
Activate Multifactor Authentication (MFA)
No matter how secure a password is, you should always keep in mind that it can be discovered. For example, if your device has a keylogger, every keystroke you make is recorded and sent to the attacker. In this case, no matter how complex the password is, its complexity won’t matter once it is transmitted to the malicious actor.
To help address this and other issues, Multi-Factor Authentication (MFA) adds an extra layer of security to your accounts by requiring another factor whenever you log in. This factor could be, for example, a One-Time Password (OTP) generated on your mobile device through an Authenticator app, which you need to enter on the website to gain access. In this case, in addition to the password, you would need your device to log into your account.
Find out more about MFA here.
Go passwordless
As we know, passwords are vulnerable and continue to pose a problem in protecting online accounts. However, there are protocols designed to address the weaknesses of passwords, making access both safer and simpler. Click here to learn more details.
Other precautions
In addition to the good practices mentioned above that are more directly related to passwords themselves, there are several other concerns you should keep in mind.
Use a secure Internet connection
It is well known that even our home internet connection is not entirely private, as the ISP (Internet Service Provider) can see where we are browsing and can even view unencrypted traffic.
Worse than this is the use of public Wi-Fi networks, such as those in cafes, airports, or hotels.
Consider using a VPN that encrypts all your traffic from your device to the VPN server you are connected to. This way, any systems in between will only see encrypted traffic and won’t be able to decipher what is being transmitted. However, you should be cautious when choosing a VPN service. Specifically, it should be audited to ensure it doesn’t keep logs of your browsing activity, because just as your ISP can see your traffic if you don’t use a VPN, so too can the VPN provider if they do keep logs.
Services such as (affiliate links) Proton VPN, NordVPN, Bitdefender VPN, among others, are recognized as trustworthy.
Only visit HTTPS sites
When you access a site with an address that begins with HTTP://, it means that the traffic between your device and the site’s server is not encrypted. In this case, if the traffic between your device and the server is intercepted, the data, including your password, is readable by third parties.
Always check if the address you are accessing begins with HTTPS:// or if there is a closed padlock icon (sometimes green) next to the address bar, just like when you visit YourInfoSec.

HTTP stands for Hyper Text Transfer Protocoland HTTPS for Hyper Text Transfer Protocol Secure. Transport Layer Security (TLS), which replaced Secure Sockets Layer (SSL) and corrected several of its vulnerabilities, is the protocol responsible for encrypting HTTPS communication.
Check the address of the site you are visiting
Is the site you are accessing really the one you intended, or is it an exact copy? Pay close attention to the address in your browser’s address bar. There are well-known cases where the similarities are so striking that users have entered their credentials on a fake site, believing they were on the genuine one. Trust me, there are exact copies where the differences escape even the most trained eyes.
To avoid being scammed, always check the address.
Notifications when you log in
Prioritize services that send notifications whenever you log in. This way, if you receive such a notification and you weren’t attempting to log in, you’ll know something is wrong and can take swift action to minimize the issue.
If the system in question does not send these notifications, check if it provides information about the last login or has a visible login log. If it does, take a moment occasionally to review it and see if everything looks good or if there’s something suspicious. If you suspect that a login isn’t yours, reset your password immediately.
Account blocking for wrong attempts and CAPTCHA
Also, prioritize services that temporarily or permanently lock your account after a certain number of failed login attempts. This way, brute force and dictionary attacks become ineffective, as these methods are already time-consuming (especially with secure passwords), and the added locks make them impractical.
Websites should also use CAPTCHA systems (Completely Automated Public Turing test to tell Computers and Humans Apart) to filter out human users from bots.
Secure password storage
Favor services that do not store your passwords. Yes, I repeat, prioritize services that do not store your passwords. Services should never store user passwords; they should store only their digests.
But this alone isn’t enough, as they would still be vulnerable to rainbow table attacks. A salt should be added to the password, and only then the password + salt should be hashed.
How do I test if my password is secure?
Password managers typically include features that indicate whether each of your passwords is secure, alerting you to those that aren’t. Some even provide statistics so you can quickly grasp the status of your credentials.
In addition to these, there are some online services that also do this, such as this one.
Conclusion
Credential discovery attacks have evolved over time, as has computational power, significantly reducing the wait time for those engaged in such activities. To address this, it’s essential to pay attention to some basic precautions described in this article. Some of these precautions can be directly implemented by the reader, while others should be enforced by the services in use. Therefore, it’s important to manage your passwords effectively and also to be aware of the quality of the services where you share your information.

